This post originally published on Citrix Blogs
The desktop-centric world is dead. Here’s why — and how — it will be replaced.
When industries shift very slowly, sometimes the most significant changes go completely unnoticed. For example, consider how the notion of the “desktop is your workspace” is pretty much becoming irrelevant (if you disagree, read on).
The point here is that cloud services, SaaS apps, and browser-based services are now really your new “workspace.” You don’t really need your desktop at all. In fact, even your desktop productivity tools, like MS Office, are now in the cloud (Office 365) and even desktops themselves (XenDesktop Essentials) can be accessed over the web.
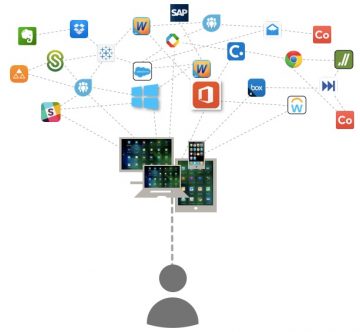
Now, if you’re in corporate IT, this evolution toward disaggregated services is leading you toward a ton of problems: multiple user logins, manual service onboarding, inconsistent security across different service providers, and, basically, loss-of-control over what apps users/employees work with. More often the problem is being referenced as cloud service sprawl.
As the desktop-centric model dissolves, there is a new model ready to take its place: the digital workspace. This will fast become the way that IT aggregates, assembles, secures and delivers unified workspace environments in this brave new cloud services world.
How we got here
The world used to be desktop-centric
For decades, workers started their “digital day” with their PCs or Macs — mostly using applications and productivity tools. The Integration model was whatever was installed locally; the Security model was whatever they had protected with their PC password. Maybe they used a browser, but 99% of the time, it was to consume information from the web. And it worked… for a while.
Then, we became browser-centric
Over time, more of our work lives were spent with browser-based applications (think SalesForce, WorkDay, SAP). Gradually, the success of cloud-delivered SaaS apps — which were soon available as apps on our phones, too — began to dominate our work days. Plus, lots of useful apps, such as Evernote and DropBox, were organically adopted by employees, creating “Shadow IT” problems within companies. Thus began the first true phase of cloud sprawl, where the digital work environment became disaggregated. Worse yet, some services had different browser requirements, users had multiple logins, and IT had little-to-no insight into who had access to what. Even still, more and more of our time was being spent “outside the desktop” using externally sourced services.
Today, nearly everything resides outside your desktop
Fast-forward to today. The vast majority of apps you use are either browser-based, fully web-based apps, or full mobile apps (particularly true when you think about how you use apps on your cell phone). The only things, really, that workers use that are “native” to the PC or Mac are productivity tools like Microsoft Office (unless you’re a digital native, you probably eschew that in favor of Google docs, yet another external service.) In fact, even Microsoft Office is being disaggregated from the PC desktop, with the prevalent use of Office 365.
So, we have to ask ourselves two questions: (a) is the desktop (as a “container” of apps) relevant anymore, and (b) if not, what becomes the new access and aggregation point for a worker’s apps and data?
IT – and users – need a new way to aggregate, secure, access, and deliver cloud services
Let’s assume we had never started with a desktop PC at all and that all of your necessary work applications were just a mix of on-premises apps, browser-based apps, mobile apps and cloud/SaaS services.
We’d want our IT departments to have a way to onboard and aggregate each service into a curated and controlled “workspace” environment. Each employee would have workspace of their own — one with a single login, with policies that controlled which apps they had access to, end even workflow tools between apps and coworkers. Even better, we’d want the workspace to ensure that apps with native UIs, browser UIs, and even device-dependent UIs would all be available consistently on any device. Best of all, we’d want this controlled “space” to follow workers around on their devices, whether they were using their laptop, a borrowed tablet, their personal phone, or any device of their choosing.
The digital workspace is real, and it’s now: Where you’ll start your “digital day”
The relatively new notion of the “secure digital workspace” is increasingly the way workers will access the resources they need, and how IT will aggregate, secure, and deliver all applications, regardless of where they’re generated or which personal devices are being used for access.
And it will be contextual and personal — you’ll have it available on all of your devices, and it will know if you’re using a secure device, if you’re on a secure network, and even whether you’re in a secure location. This means that you might not have full access rights to certain apps based on where you are or what network you’re on, or the system may change the method of delivery to ensure better security. It might even notice you’re simultaneously logged into two devices in two countries and raise a security flag.
For workers, this approach will simplify how they get to all the apps and data they need to be productive, and will make it possible to easily collaborate with coworkers, contractors, partners, and customers. And it will ensure consistency by bringing disparate applications and data into a user-centric, context-aware environment. Finally, it will optimize their experience, performance and security across any device, platform or network — regardless of the platform for which the original app may have been designed.
For corporate IT, it will help them restore control over their employee’s digital environment because a secure digital workspace ensures better, more consistent control over on-boarding, aggregating, and managing access across hybrid cloud services, regardless of their source. And overall, this unified approach reduces risk for companies because the entire workspace is surrounded by a “Secure-Digital Perimeter” across infrastructure, apps, delivery networks, and devices.
If this sounds interesting, I encourage you to look into the possibilities, such as using the Citrix workspace to aggregate, secure, access, and deliver this new world of possibilities to workers near you.








No comments:
Post a Comment